
Rewriting History: A Brief Introduction to Long Range Attacks | by Evangelos Deirmentzoglou | ICO Security

Rewriting History: A Brief Introduction to Long Range Attacks | by Evangelos Deirmentzoglou | ICO Security

Rewriting History: A Brief Introduction to Long Range Attacks | by Evangelos Deirmentzoglou | ICO Security

Investigating Long Range Attack. Theoretical attack against proof of… | by Lior Yaffe | HackerNoon.com | Medium

How PoS networks are protected from 51% attacks | by Cardanians.io (CRDNS pool) | Coinmonks | Medium

Rewriting History: A Brief Introduction to Long Range Attacks | by Evangelos Deirmentzoglou | ICO Security

Rewriting History: A Brief Introduction to Long Range Attacks | by Evangelos Deirmentzoglou | ICO Security

Rewriting History: A Brief Introduction to Long Range Attacks | by Evangelos Deirmentzoglou | ICO Security




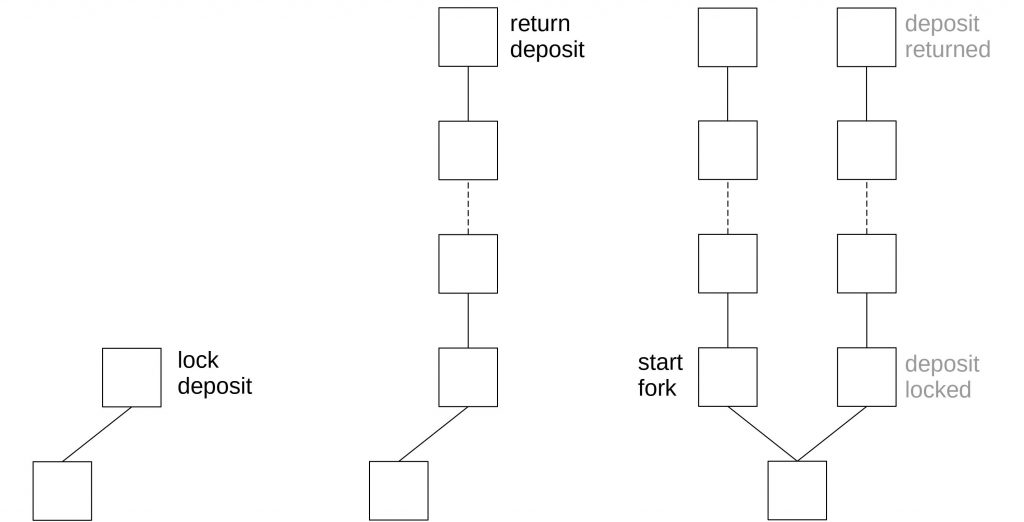
![PDF] A Survey on Long-Range Attacks for Proof of Stake Protocols | Semantic Scholar PDF] A Survey on Long-Range Attacks for Proof of Stake Protocols | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/2b0ec33ddbaa535ca29db6c2af263eb0973c4bd9/9-Figure6-1.png)


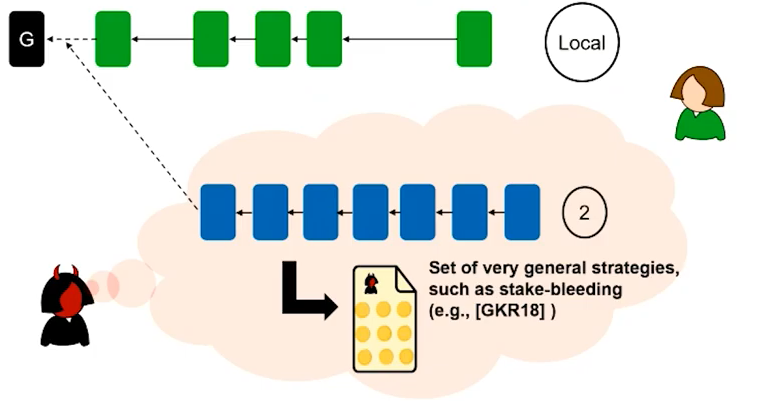

![PDF] A Survey on Long-Range Attacks for Proof of Stake Protocols | Semantic Scholar PDF] A Survey on Long-Range Attacks for Proof of Stake Protocols | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/2b0ec33ddbaa535ca29db6c2af263eb0973c4bd9/6-Figure2-1.png)
